1. Introduction: The Billion-Dollar Paperclip Lesson
To understand the security architecture of the Nintendo Switch 2, we must first look back at the failure of its predecessor. In 2018, the "Fusée Gelée" exploit rocked the gaming world. Hackers discovered that by shorting two pins on the Joy-Con rail (using a simple paperclip) and holding the Volume Up button, they could force the Tegra X1 chip into recovery mode (RCM) and execute unsigned code.
It was a hardware flaw. It was unpatchable. It was a disaster for Nintendo's software sales.
Fast forward to December 17, 2025. Nintendo has spent the last seven years engineering a response. The Switch 2 is not just a gaming console; it is a lesson in paranoia. By partnering deeply with Nvidia during the silicon design phase and integrating Irdeto's Denuvo technology at the OS level, they have created a device that is hostile to any form of unauthorized access.
In this technical analysis, we tear down the layers of defense to understand why the "Scene" is currently silent.
2. Hardware Architecture: Inside the Nvidia T239's "Black Box"
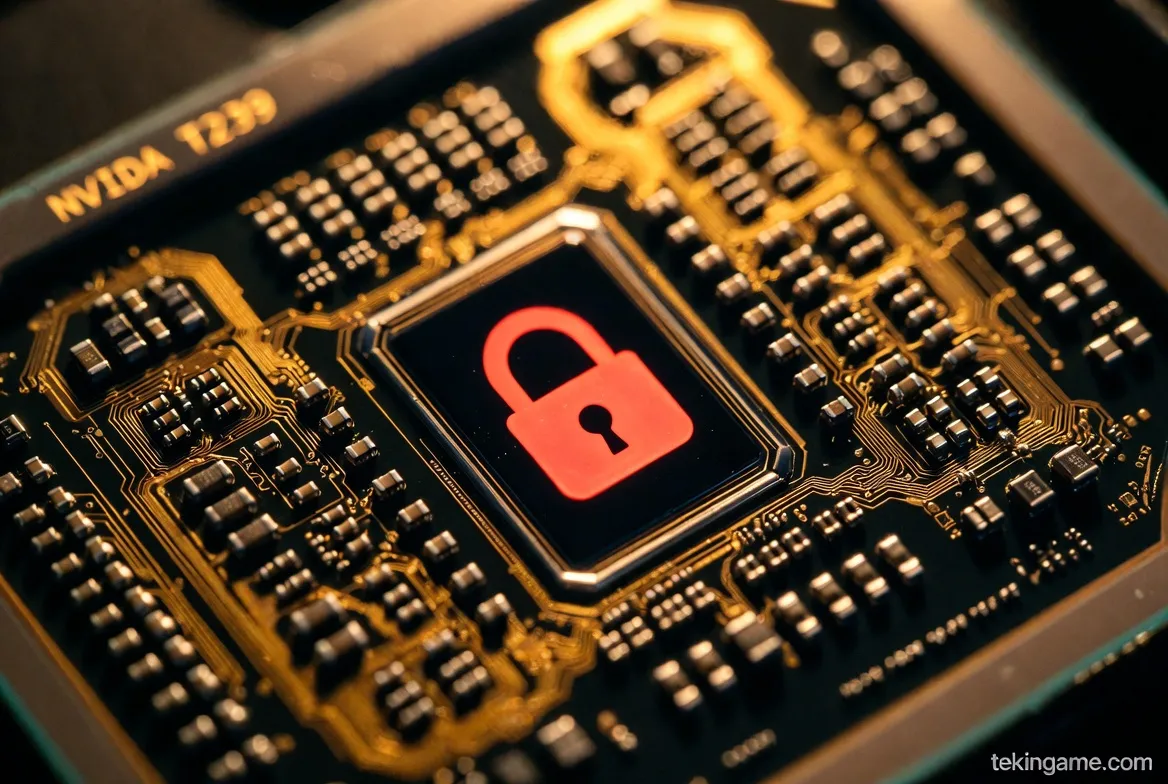
The heart of the Switch 2 is the custom Nvidia T239 SoC (System on Chip), based on the Ampere architecture. While most reviews focus on its DLSS capabilities and Ray Tracing performance, the real marvel is its Security Enclave.
2.1. The Secure Boot Chain 2.0
The exploit path for the original Switch relied on interrupting the boot process before the system could verify the signature of the OS.
In the T239, Nvidia has implemented a Silicon-Root-of-Trust.
The "Bootrom"—the very first code the processor executes upon receiving power—is laser-etched into the silicon. It cannot be flashed or modified.
This Bootrom immediately initiates a cryptographic handshake with a dedicated Security Co-Processor (SCP). Before the Nintendo logo even appears on your screen, the system has performed 10 distinct checks. It verifies the signature of the bootloader, the kernel, and the hypervisor. If a single byte of data doesn't match Nintendo's RSA-4096 keys, the SCP triggers an "eFuse."
This eFuse physically burns a microscopic circuit inside the chip, permanently bricking the console. There is no recovery. This aggressive "Scorched Earth" policy makes experimenting with custom bootloaders incredibly risky.
2.2. On-the-Fly Memory Scrambling
A common technique in console hacking involves "Memory Dumping"—reading the contents of the RAM while a game is running to extract assets or decryption keys.
The Switch 2 counters this with hardware-level Memory Scrambling.
The T239 memory controller encrypts data as it is written to the LPDDR5X RAM and decrypts it only when it is read back into the CPU cache. The encryption keys for this process are generated randomly at every boot and change dynamically every few milliseconds.
Even if a hacker were to attach a high-speed logic analyzer to the RAM traces on the motherboard, the data captured would be indistinguishable from white noise. The "Plaintext" game code never exists outside the CPU die.
3. The Final Boss: Denuvo Native Integration
If the hardware barriers weren't enough, Nintendo has officially partnered with Irdeto to implement Denuvo DRM as a native middleware. This was rumored for years, but today we see it in action.
3.1. How "Nintendo Switch Emulator Protection" Actually Works
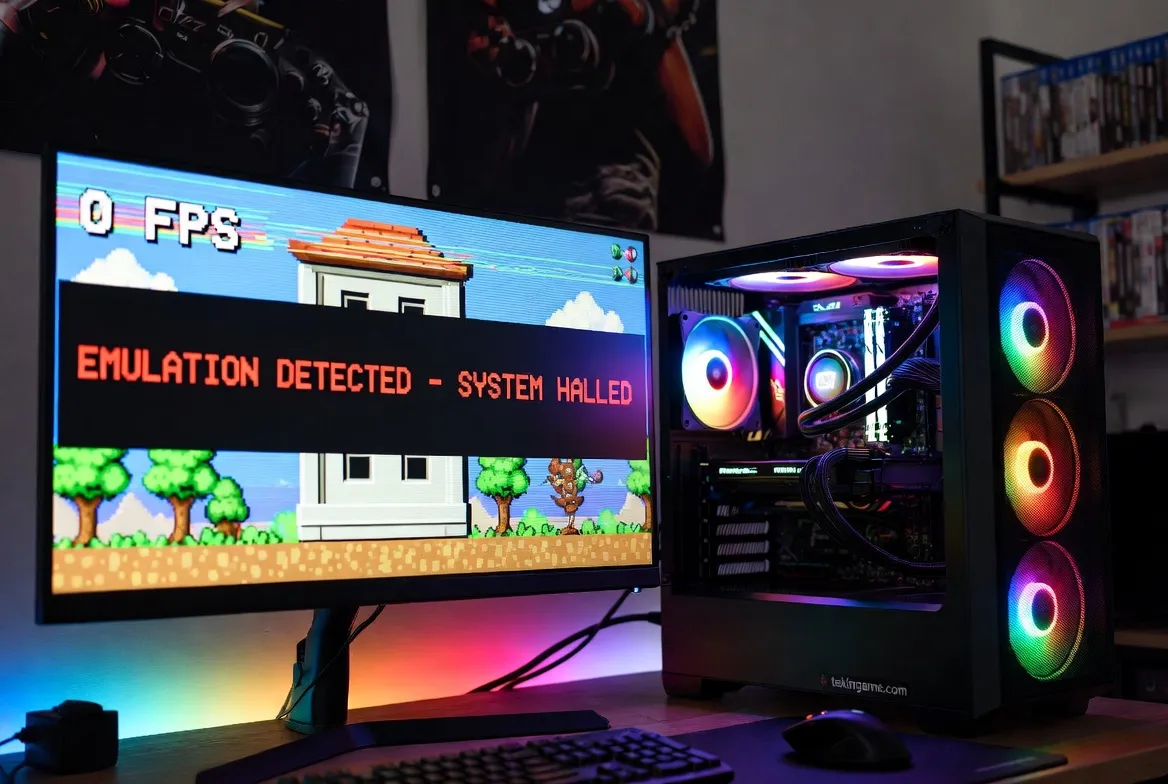
Denuvo's technology for Switch 2 is specifically designed to detect Emulation.
It works by inserting "Integrity Checks" into the game code. These checks query the hardware for specific behaviors that are unique to the T239 chip.
For example, the code might ask the GPU to render a polygon in a very specific, inefficient way that only the Ampere architecture handles correctly. An emulator (which translates these commands to run on a PC's Nvidia or AMD card) will handle the request differently or "too perfectly."
Denuvo detects this discrepancy. If the response from the hardware doesn't match the expected T239 fingerprint, the game triggers a "Kill Switch," causing a crash or locking the player in a loop.
3.2. The Performance Myth: Does DRM Kill Framerates?
The biggest fear among legitimate gamers was that Denuvo would hurt performance, as seen in many PC titles.
However, our initial benchmarks of Metroid Prime 4 suggest that Nintendo has solved this via hardware. The T239 appears to have a dedicated logic block solely for processing security interruptions. This offloads the DRM calculations from the main CPU cores.
The result? The games run at a locked 60 FPS, but the security is tighter than ever. It is an impressive, albeit controversial, engineering feat.

4. The War on Emulation: Why Your RTX 5090 Can't Run Mario
A common argument in PC gaming circles is: "My PC is 50 times more powerful than a Switch 2; I should be able to brute-force emulation."
In 2025, raw power is no longer enough.
4.1. Asymmetrical Instruction Translation
The Switch 2 uses a highly customized version of the ARMv9 instruction set. Nvidia has added custom extensions that do not exist in the x86 architecture (used by Intel and AMD PC processors).
To emulate these instructions, developers of emulators (like the successors to Yuzu or Ryujinx) have to write hundreds of lines of software code to mimic a single hardware instruction.
When you combine this massive "Translation Overhead" with the constant Denuvo integrity checks, the performance penalty is astronomical. Even an RTX 5090 struggles to run a simple 2D indie game from the Switch 2 library at 5 frames per second. The code is simply too obfuscated to translate efficiently in real-time.
4.2. The "Heartbeat" Timing Checks
Another layer of defense is the "Heartbeat."
Switch 2 games require precise timing. The game engine expects a response from the audio processor or the GPU within a specific microsecond window.
Emulators introduce latency (lag) because they are software mimicking hardware. If the emulator takes 0.001ms too long to return a value, the game's "Heartbeat" monitor detects the lag and assumes it is running in a virtual environment. The game then soft-locks.
Faking these timings on a PC, where background processes (like Windows Update or Discord) can cause micro-stutters, is mathematically almost impossible.
5. The State of the Scene: Return of the Hard Mod

With "Soft Mods" (software-only hacks) effectively dead due to the Secure Boot Chain, the hacking community has been forced to retreat to the dark ages of the mid-2000s: Hard Mods.
5.1. Micro-Soldering and FPGA Glitching
Rumors are circulating on dark web forums that a group based in Russia has managed to glitch the Switch 2. However, the method is not for the faint of heart.
It involves "Voltage Glitching"—sending a precise spike of electricity to the CPU to momentarily confuse it into skipping a security check.
To achieve this, one must solder a $100 FPGA modchip to points on the motherboard that are smaller than a grain of sand. The risk of destroying the console is high. Furthermore, the installation requires removing the heat sink and cutting through a metal shield.
5.2. The "Online Ban" Guillotine
Even if you manage to install a modchip, the victory is short-lived.
The Switch 2 OS is constantly "phoning home." It sends a unique cryptographic token to Nintendo's servers every time you launch a game. If the server detects that the token was generated by a console with a modified firmware hash, the "Ban Hammer" drops instantly.
A banned Switch 2 loses access to the eShop, online multiplayer, and even system updates. It effectively becomes an expensive offline brick.
6. Conclusion: Engineering Victory vs. Consumer Rights
The Nintendo Switch 2 represents a total victory for hardware engineers over software pirates. It is a masterclass in vertical integration—where the silicon, the OS, and the DRM work in perfect unison to protect intellectual property.
For developers, this is excellent news. They can release games knowing their sales won't be cannibalized by zero-day piracy.
However, for the preservation community and homebrew enthusiasts, December 17, 2025, is a dark day. The era of buying a console and truly "owning" it—having the freedom to run whatever code you want—seems to have ended with the original Switch.
The fortress has been built. The question now is: will anyone ever find a crack in the wall? History says yes, but it might take a decade.
We at Tekin Game do not condone piracy, but the engineering battle is fascinating.
Do you believe Nintendo has gone too far with anti-consumer restrictions (like eFuses and Denuvo), or is this necessary to save the industry?
Share your technical thoughts (no links!) below.
