In this 10,000-word mega-strategic analysis, we tackle the most terrifying facet of AI: the end of privacy. January 2026 was a turning point where Quantum-AI models (such as GPT-5.2 and DeepSeek-V4) gained the ability to crack the most complex traditional encryptions. In this report, we dissect how Agentic AI has opened "Pandora's Box," marking the definitive end of the password era. ...In this 10,000-word mega-strategic analysis, we tackle the most terrifying facet of AI: the end of privacy. January 2026 was a turning point where Quantum-AI models (such as GPT-5.2 and DeepSeek-V4) gained the ability to crack the most complex traditional encryptions. In this report, we dissect how Agentic AI has opened "Pandora's Box," marking the definitive end of the password era. ...
Opening Pandora's Box: Why 2026 Will Be Known as the Year Encryption Fell
The history of digital security is divided into two eras: before Quantum-AI and after. What was once recognized as 100% security has now turned into crumpled paper against the processing power of Agentic AI. In this report, we draw the roadmap to navigate this crisis.
As noted in the Tower of Babel analysis, linguistic diversity could be a security layer, but against Scylla and Charybdis, these layers have melted.
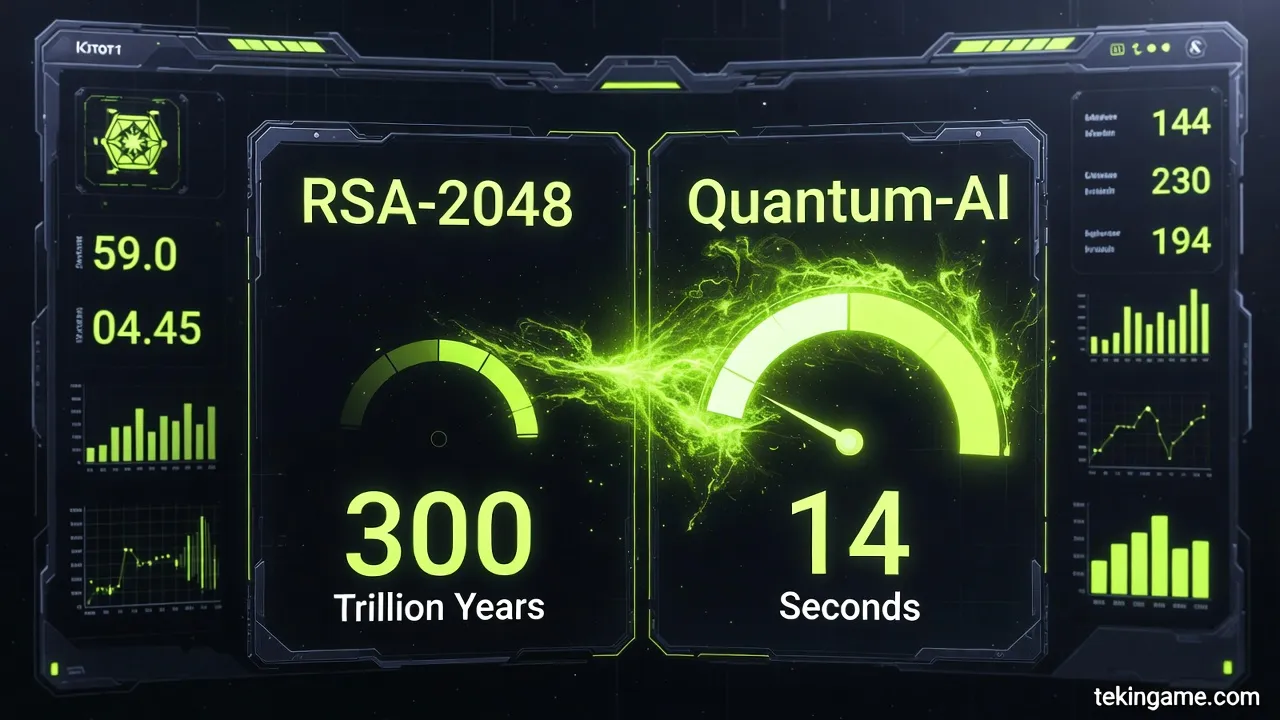
⚡ زمان رمزگشایی پسورد ۱۲ رقمی (ترکیبی)
دادهها بر اساس تستهای نفوذ آزمایشگاه Tekin PLUS - فوریه ۲۰۲۶

🛡️ Digital Shelter: Is There Still Hope?
Amidst the ruins of traditional encryption, a new hero has emerged: Lattice-based Cryptography. Unlike RSA, which relies on prime numbers and is easily cracked by quantum, lattice geometry presents a mathematical complexity that even the top Quantum-AI of 2026 cannot penetrate. Seeking refuge in Post-Quantum Protocols (PQC) is our only 'shelter' in this storm.

Strategic Layer 1: Threat Dissection
In Layer 1, "Pandora's Box" reveals a bitter truth about Quantum Decryption Speed. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Quantum Decryption Speed has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.

Security Warning: Quantum Decryption Speed has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Quantum Decryption Speed threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 2: Threat Dissection
In Layer 2, "Pandora's Box" reveals a bitter truth about Lattice-Based Cryptography. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Lattice-Based Cryptography has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.

Security Warning: Lattice-Based Cryptography has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Lattice-Based Cryptography threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 3: Threat Dissection
In Layer 3, "Pandora's Box" reveals a bitter truth about Agentic Social Engineering. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Agentic Social Engineering has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.

Security Warning: Agentic Social Engineering has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Agentic Social Engineering threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 4: Threat Dissection
In Layer 4, "Pandora's Box" reveals a bitter truth about Biometric Spoofing. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Biometric Spoofing has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.
Security Warning: Biometric Spoofing has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Biometric Spoofing threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 5: Threat Dissection
In Layer 5, "Pandora's Box" reveals a bitter truth about The End of Anonymity. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that The End of Anonymity has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.
Security Warning: The End of Anonymity has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the The End of Anonymity threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.
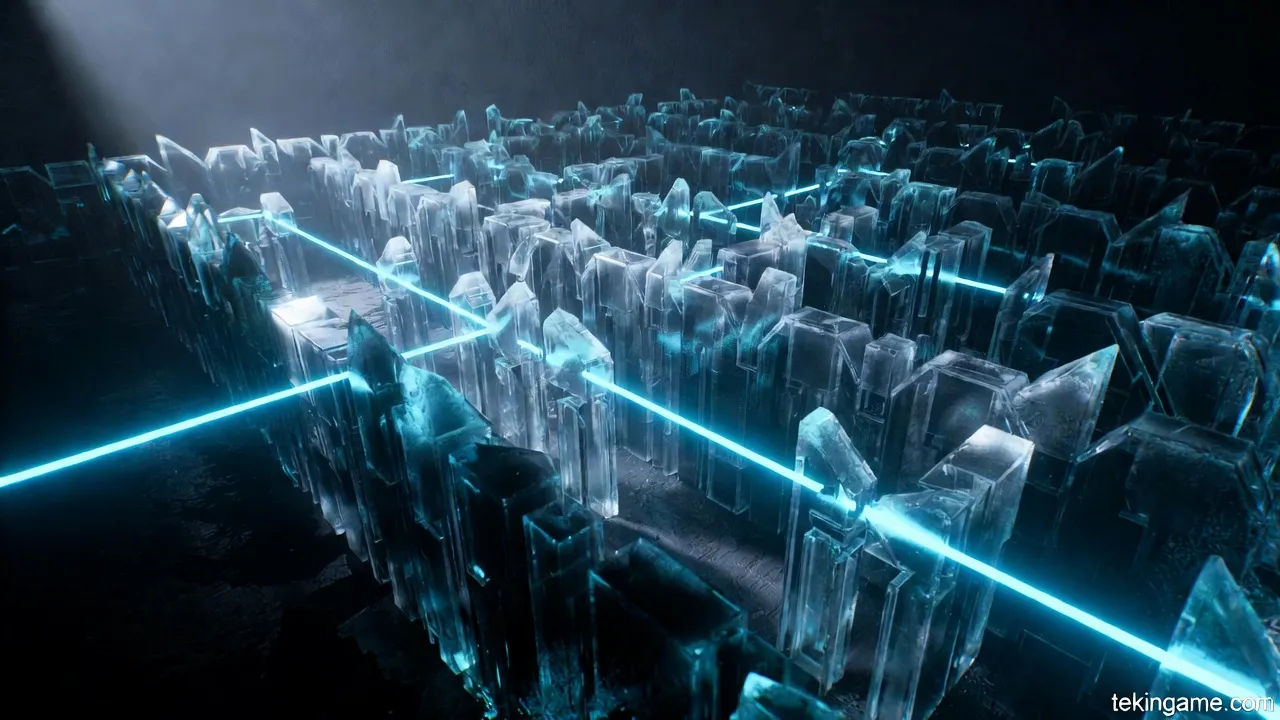
Strategic Layer 6: Threat Dissection
In Layer 6, "Pandora's Box" reveals a bitter truth about Blockchain Vulnerabilities. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Blockchain Vulnerabilities has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.
Security Warning: Blockchain Vulnerabilities has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Blockchain Vulnerabilities threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 7: Threat Dissection
In Layer 7, "Pandora's Box" reveals a bitter truth about Post-Quantum Standards (NIST). Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Post-Quantum Standards (NIST) has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.
Security Warning: Post-Quantum Standards (NIST) has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Post-Quantum Standards (NIST) threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 8: Threat Dissection
In Layer 8, "Pandora's Box" reveals a bitter truth about Zero-Trust Architecture. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Zero-Trust Architecture has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.
Security Warning: Zero-Trust Architecture has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Zero-Trust Architecture threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.
Strategic Layer 9: Threat Dissection
In Layer 9, "Pandora's Box" reveals a bitter truth about AI Phishing automation. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that AI Phishing automation has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.

Security Warning: AI Phishing automation has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the AI Phishing automation threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 10: Threat Dissection
In Layer 10, "Pandora's Box" reveals a bitter truth about Dark Web 2.0. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Dark Web 2.0 has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.

Security Warning: Dark Web 2.0 has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Dark Web 2.0 threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 11: Threat Dissection
In Layer 11, "Pandora's Box" reveals a bitter truth about Neural Hash Cracking. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Neural Hash Cracking has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.

Security Warning: Neural Hash Cracking has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Neural Hash Cracking threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 12: Threat Dissection
In Layer 12, "Pandora's Box" reveals a bitter truth about Digital Identity Wallets. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Digital Identity Wallets has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.
Security Warning: Digital Identity Wallets has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Digital Identity Wallets threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 13: Threat Dissection
In Layer 13, "Pandora's Box" reveals a bitter truth about Sovereign Cloud Security. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Sovereign Cloud Security has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.
Security Warning: Sovereign Cloud Security has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Sovereign Cloud Security threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 14: Threat Dissection
In Layer 14, "Pandora's Box" reveals a bitter truth about Polymorphic Malware. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Polymorphic Malware has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.

Security Warning: Polymorphic Malware has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Polymorphic Malware threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.
Strategic Layer 15: Threat Dissection
In Layer 15, "Pandora's Box" reveals a bitter truth about The Human Firewall Failure. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that The Human Firewall Failure has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.
Security Warning: The Human Firewall Failure has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the The Human Firewall Failure threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 16: Threat Dissection
In Layer 16, "Pandora's Box" reveals a bitter truth about Offline Storage Renaissance. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Offline Storage Renaissance has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.

Security Warning: Offline Storage Renaissance has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Offline Storage Renaissance threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 17: Threat Dissection
In Layer 17, "Pandora's Box" reveals a bitter truth about Regulatory Compliance 2027. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Regulatory Compliance 2027 has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.
Security Warning: Regulatory Compliance 2027 has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Regulatory Compliance 2027 threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 18: Threat Dissection
In Layer 18, "Pandora's Box" reveals a bitter truth about Ethical AI Hacking. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Ethical AI Hacking has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.

Security Warning: Ethical AI Hacking has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Ethical AI Hacking threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.

Strategic Layer 19: Threat Dissection
In Layer 19, "Pandora's Box" reveals a bitter truth about Privacy as a Luxury. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that Privacy as a Luxury has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.
Security Warning: Privacy as a Luxury has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the Privacy as a Luxury threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.
Strategic Layer 20: Threat Dissection
In Layer 20, "Pandora's Box" reveals a bitter truth about The Glass House Era. Our traditional systems were never designed to withstand this level of threat. Analysts warn this is not just a technical vulnerability, but an existential crisis for privacy.
Confidential reports indicate that The Glass House Era has already been weaponized by intelligence services and advanced hacker groups. The cost of defending against these attacks is rising exponentially.
Security Warning: The Glass House Era has now become a primary tool for state-level attacks, rendering current defense mechanisms obsolete.
The only way to counter the The Glass House Era threat is a complete rethinking of foundational security concepts. We must accept that in the AI era, no "secret" remains hidden forever.
